Cybersecurity
Practitioner's Profile
From a young age, I’ve always felt called to fight the good fight. That calling led me to join the Texas Army National Guard at just 17 years old, becoming an Intelligence Analyst while still a junior in high school. During my nine years of service, I deployed to Iraq, earned the rank of Sergeant, and became a proud Wounded Warrior. My time in the military shaped my foundation—discipline, resilience, integrity, and an unshakeable drive to protect others.
When I transitioned out of the Army, that mission didn’t leave me. I still wanted my work to matter. I still wanted to defend, to serve, and to stand on the front lines of something meaningful. That purpose guided me straight into the world of cybersecurity.
Today, with eight years of experience in the cybersecurity field, I can confidently say I found the perfect extension of my calling. I’ve worked with Fortune 500 companies as a Security Analyst, Security Engineer, and Incident Response specialist—protecting organizations from real, evolving, and increasingly dangerous cyber threats. I take pride in being part of every layer of defense, ensuring that people, businesses, and data stay protected.
This isn’t just a career for me. It’s a passion. It’s purpose. It’s me continuing to fight the good fight.
If you’re reading this, I hope I get the opportunity to fight the good fight for you, too.

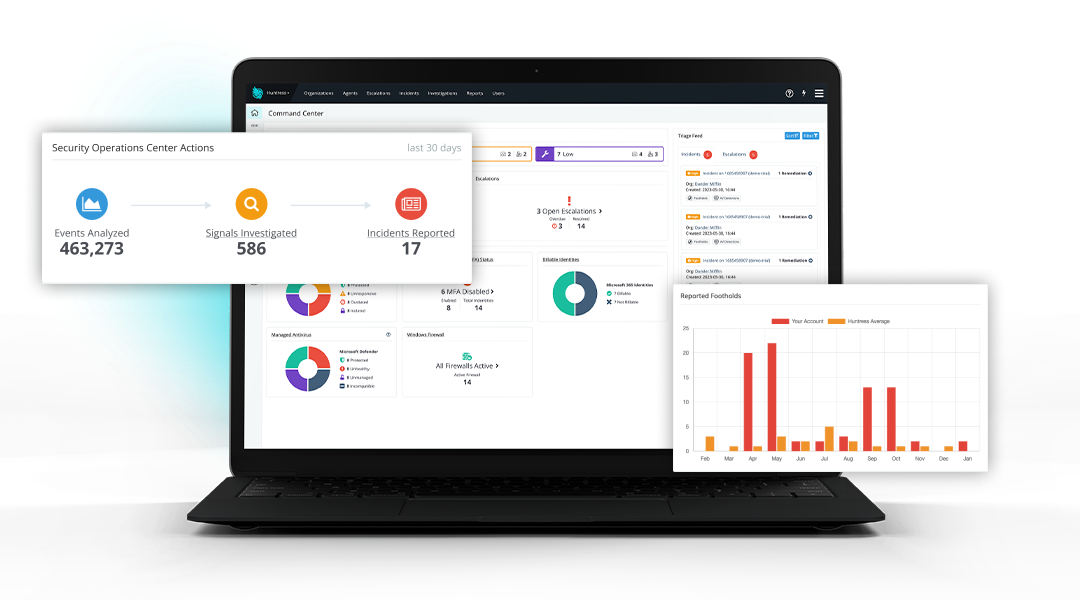
What We Offer
Managed Endpoint Detection & Response (EDR)
Protect every endpoint in your environment with Managed EDR that combines advanced technology with real human expertise. Our always-on security operations team proactively hunts threats, validates alerts, and executes rapid response actions — ensuring attackers are stopped before they can disrupt your business. All the power of enterprise-grade endpoint protection, delivered at a cost that works for growing organizations.
24/7 Human-Led SOC
Continuous monitoring and threat hunting by certified analysts — not just automation.Full Threat Lifecycle Coverage
Detection, investigation, containment, and remediation support from start to finish.Rapid Incident Response
One-click isolation and response actions to stop active threats fast.Industry-Leading Accuracy
Less than 1% false-positive rate to reduce alert fatigue and operational overhead.Advanced Endpoint Protection
Real-time behavioral analytics, ransomware prevention, and exploit blocking.Affordable Enterprise-Grade Security
Optimized cost model designed for growing and mid-size organizations.Exceptional Support Experience
Direct 24/7 access to your cyber security expert, Fabian
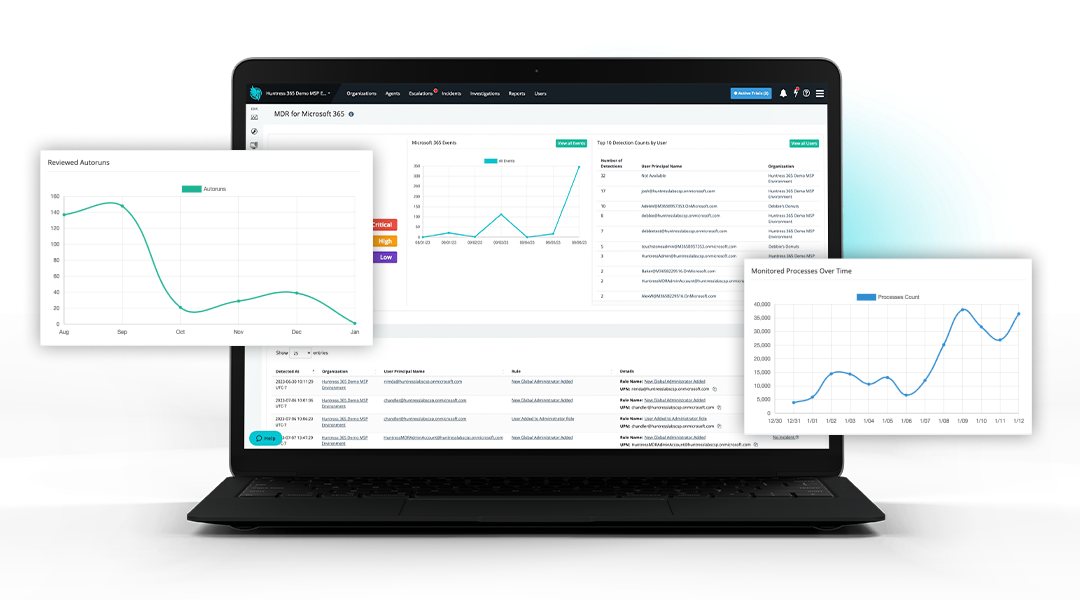
Managed Identity Threat Detection & Response (ITDR)
Protect the identities at the core of your business with Managed ITDR designed specifically for Microsoft 365 environments. Our analysts continuously monitor user behavior to detect credential misuse, unauthorized access attempts, and identity-driven attacks — stopping threats before they can compromise communications or sensitive data. We deliver high-fidelity alerts, rapid response guidance, and proactive threat hunting to keep your organization secure and productive.
- Microsoft 365 Identity Protection
Shields accounts from session hijacking, credential theft, malicious inbox rules, account takeover, and business email compromise (BEC). - 24/7 Monitoring & Expert Analysis
Continuous identity telemetry review by a human-led SOC to quickly detect abnormal or unauthorized activity. - Precision Alerting
Noise is filtered out — you’re only alerted when activity is confirmed as truly malicious, minimizing operational burden. - Rapid Containment & Response
Expert guidance and recommended actions to stop identity-based attacks before they propagate. - Threat Hunting for Identity Abuse
Proactive detection of lateral movement, suspicious login patterns, and privilege escalation attempts. - Business Continuity Focused
Protects your users, your data, and your communication channels without slowing down productivity.
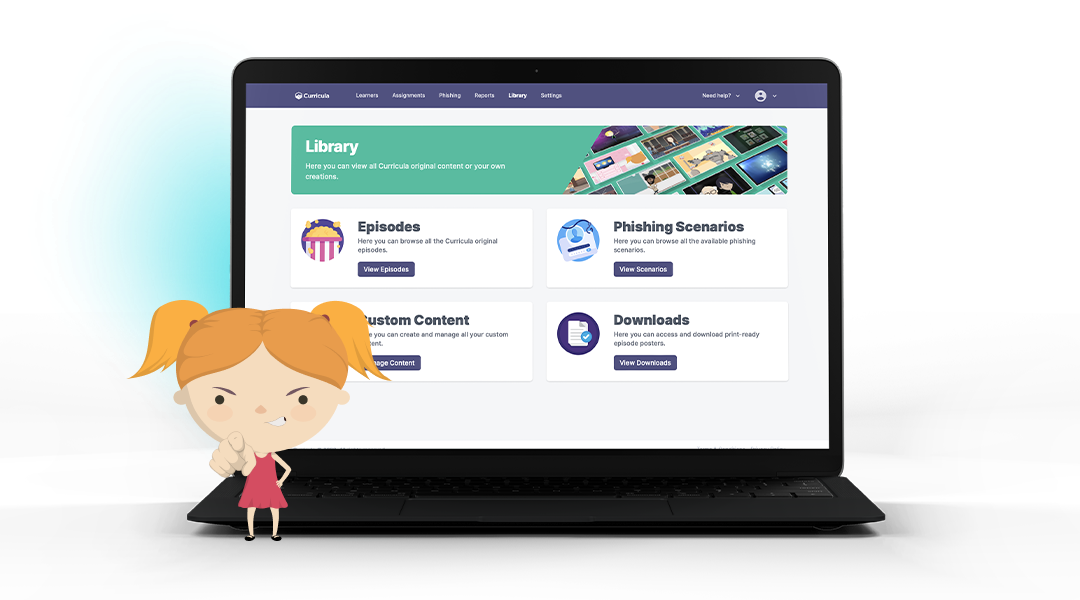
Managed Security Awareness Training
Transform your employees into your strongest line of defense with Security Awareness Training that actually sticks. Our managed program combines expert-driven administration with engaging, story-based content that improves retention and drives lasting behavioral change. Easy to deploy and effortless to manage, it helps reduce human-driven risk while strengthening your overall security culture.
- Fast Deployment & Low Maintenance
Launch the program in minutes with minimal internal effort — or fully outsource to our security experts. - Expert-Driven Program Management
End-to-end support including lesson curation, learner tracking, and managed phishing simulations. - Engaging, Story-Based Learning
Training is delivered through memorable episodic content created by award-winning animators — improving retention and reducing user fatigue. - Behavioral Change Focused
Reinforces real-world best practices to lower human-risk factors such as phishing clicks and credential misuse. - Flexible Administrative Control
Easily manage training internally if preferred, with simple deployment and automation at scale. - Ongoing Improvement & Reporting
Insightful analytics to measure progress, prove compliance, and continuously strengthen your security culture.
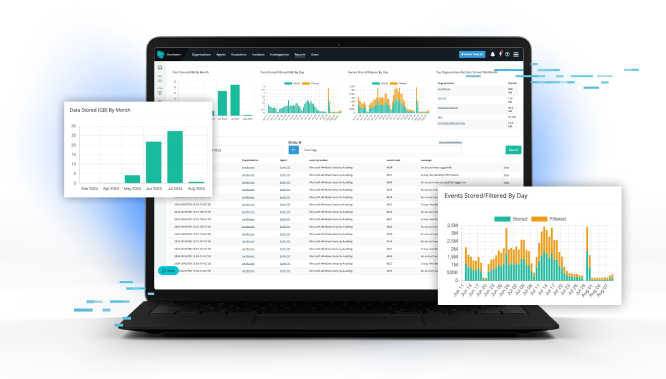
Managed Security Incident & Event Management (SIEM)
Stay ahead of evolving threats with Managed SIEM that delivers full-spectrum visibility and expert-led detection across your entire environment. Our security team monitors critical log data 24/7, cutting through the noise to surface what truly matters — and responding fast when malicious activity is confirmed. Built to simplify compliance and strengthen defense without added complexity, our solution brings enterprise-grade SOC capabilities within reach for growing organizations and MSPs alike.
- 24/7 Human-Led SOC & Threat Hunting
Around-the-clock monitoring, investigation, and threat hunting by expert analysts, not just automated alerts. - Smart Filtering — Less Noise, More Signal
Proprietary filtering engine discards irrelevant log noise and surfaces only security-relevant events, reducing alert fatigue and false positives. - Comprehensive Log Ingestion & Visibility
Ingests logs from firewalls, VPNs, identity systems, password managers, endpoints, and more — giving a unified view across your environment. - Rapid Deployment & Predictable, Transparent Pricing
Get enterprise-grade SIEM capabilities without the complexity or surprise costs of traditional SIEMs. - Long-Term Log Retention & Compliance Support
Retain data up to 7 years to meet regulatory needs (PCI-DSS, CMMC, etc.), with audit-ready reporting and easy search for forensic analysis. - Fast Incident Response & Actionable Remediation
Once a threat is confirmed, Huntress SOC delivers actionable alerts and can help with containment and remediation — enabling response earlier in the attack chain. - Scalable and Accessible for SMBs and MSPs
Designed to bring enterprise-grade security to growing companies and managed service providers without heavy infrastructure or full in-house teams.
